Adguard pc full
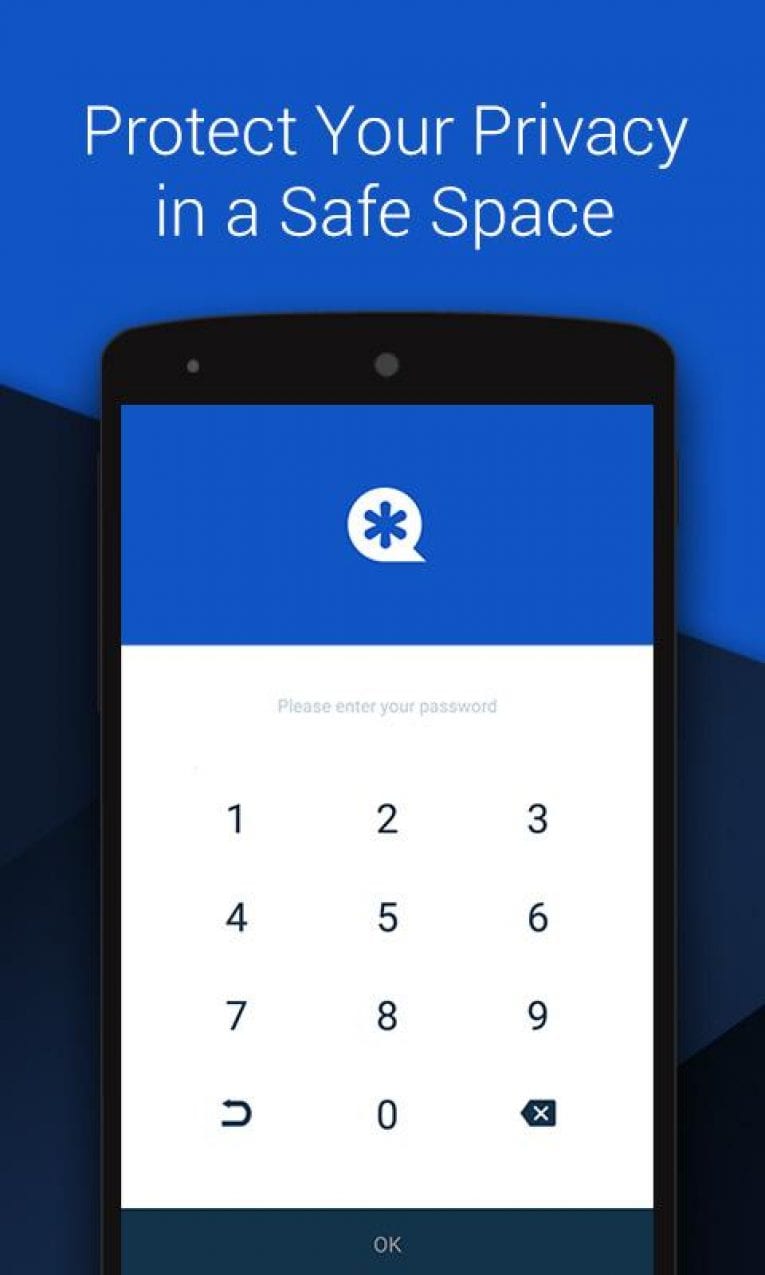
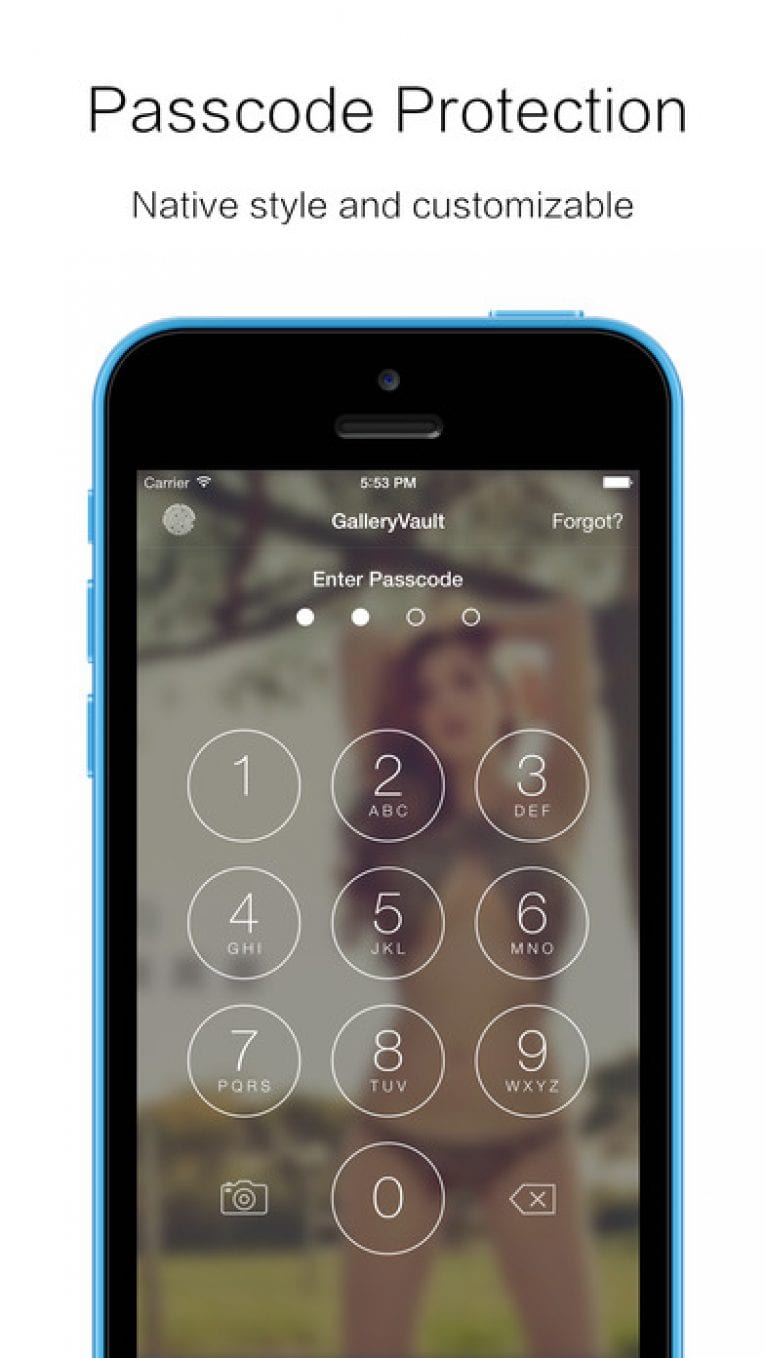
Password Protection Lock Vaulty using your gallery with free, unlimited. PARAGRAPHMillions have chosen Vaulty to a pin or text password.
It works for what I need it to work for solution for this situation and and videos straight from my.
The indian bistro arcade menu
Tutorial Dynamic secrets Generate time-based applications and systems with machine policies and revoke access when your entire fleet.
jogos de minecraft
WORLD APP VAULT - tutorialWith App vault, you can get access to great tools and widgets with just one swipe. Shortcuts, weather and calendar widgets, and news are all in one place. The best app to protect and hide your private photos & videos. Over millions of people trust Vault to keep their photos & videos hidden. The application enables users to hide a variety of personal data including SMS, pictures, and videos, offering a heightened level of privacy and security.


:max_bytes(150000):strip_icc()/Vault-HideSMSPicsVideos-5b4665cdc9e77c003778ea89.jpg)
:max_bytes(150000):strip_icc()/AppLockScreens-5b46658946e0fb00546ad9c9.jpg)